What is Phishing ?
Phishing is a play on the word “fishing,” as it is a way of “throwing out bait” to see who bites. Phishing is a method of sending a user (or many users) digital correspondence that appears legitimate but is actually meant to lure a potential victim into providing some level of personal information for nefarious purposes, including identity or monetary theft. The phishing scheme could use email, text, or web page.
Phishing emails are the most notorious forms of phishing campaigns. The bad actor will send a fake email that will contain links to false websites that appear to be associated with a legitimate business, but is being used to gather anything from passwords, to social security or account numbers. There are other forms of phishing campaigns and techniques that are used to track potential victims, including vishing, SMiShing, spy-phishing, watering hole attacks, even spam. SMS phishing (or smishing/SMiShing) is a phishing campaign that uses a bait text message to lure potential victims. Spear-phishing uses an email that has more specific information than a standard phishing email. The attacker will spend time researching the potential victims online and social media presence to gather information that will allow them to create a false sense of familiarity. Vishing uses telephone communications to social-engineer personal information. A watering hole attack is focused on a particular group, eventually affecting members of that group. Spam is a well known email type, and spy-phishing is using a phishing method to install spyware onto a potential victim’s computer.
Pharming is similar to phishing, with the same overall intent. Phishing is more of a social engineering attack, whereas pharming uses sophisticated means to redirect traffic from one website to another. Bad actors poison or corrupt DNS servers to compromise legitimate websites. Both phishing and pharming are used to collect sensitive user information.
Phishing Examples
As previously stated, the use of an email with malicious links is the most common form of phishing. Phishing techniques were described as far back in 1987, but the term was first used in 1995/1996. Remember AOL? There was a hacker tool called AOHell that was used to create fake accounts that phishers could use to instant-message customers, posing as account staff and asking the users to verify their account information and provide their passwords for security purposes. The fake accounts were created using randomized credit card number generator within the AOHell tool. AOL eventually put up warnings on their email and IM services that “no one working at AOL will ask for your password or billing information” to try and protect their customers.
Some other early phishing scams were in 2003 when emails that looked to be official correspondence from eBay stated that the user needed to make updates to their accounts or else their privileges would be suspended. They were directed to click the link in the email to update their information. The link took them to a fraudulent website that looked like the eBay site, but of course was a different URL address. Many users were fooled by the legitimacy not only of the email but of the website as well.
Over the years, phishing campaigns have matured and become even more sophisticated. The scams make it a point to use the most popular technologies or websites at the time. The eBay scam was so successful because in 2003 eBay was the new, exciting platform, with a surge of users. Some of the current phishing attempts may try to spoof the Amazon, Apple, PayPal, or Google websites, as they are the hottest and most used currently. Here is an image of a recent Amazon phishing attempt:
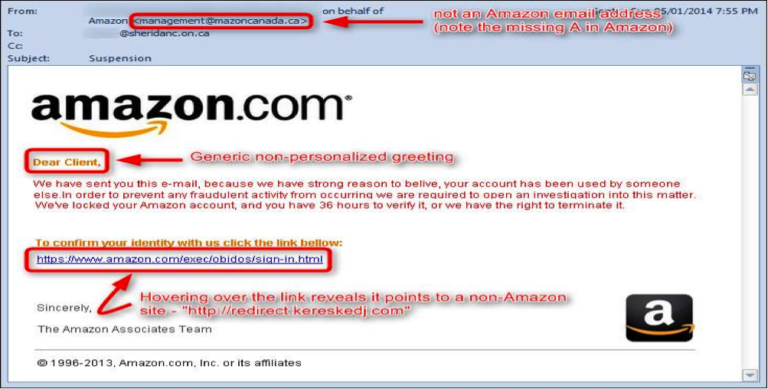 The issues with the email are highlighted, but the embedded logos, signature lines, and copyright information give the email some validity, and could fool someone who didn’t take a deeper look.
The issues with the email are highlighted, but the embedded logos, signature lines, and copyright information give the email some validity, and could fool someone who didn’t take a deeper look.
Here is a screenshot of a recent Netflix phishing scam:
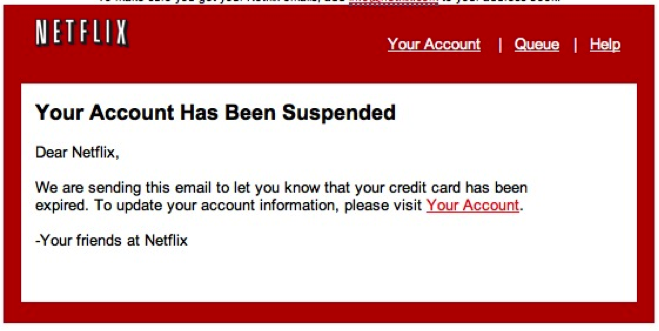 Without doing any investigation, examining the links, or looking at the “To” line in the email for clues, this also appears legitimate. This is the Netflix logo to perfection.
Without doing any investigation, examining the links, or looking at the “To” line in the email for clues, this also appears legitimate. This is the Netflix logo to perfection.
Phishing Awareness
>
APWG is an organization that gathers current statistics concerning phishing attacks. According to their collected data, phishing attacks continued to increase in 2016. They found that the number of phishing websites increased by over 250% from the end of 2015. By the end of March, they found over 123,555 unique phishing websites. They also had consumers forward suspected phishing emails to them, and they received over 229,265 unique emails. The United States is still the country hosting the most phishing websites; so American users, beware! With the increase in phishing scams, it’s important to make sure you keep your employees appraised in phishing awareness, antivirus software up to date, as well as the phishing filters within your browsers. A phishing filters is a feature within the browser that consistently monitors a database of known phishing sites. The features run in the background, but you need to be sure that you patch your browser as security patches are released. To ensure you have phishing filters running, follow your browser’s instructions.
Keeping your antivirus, security patches and browser settings up to date is a great practice, but one of the best ways companies and the general public can protect their assets is in implementing security training along with best practices into their routines. Phishing campaigns change rapidly and are becoming more sophisticated. Many companies have performed corporate phishing campaigns to see how susceptible their users are to these attacks, and to train them on how to spot the real thing. Training is the only way to keep up with current trends and best practices.
Conclusion
Phishing is a form of social engineering used to collect personal information from the intended victim. Phishing campaigns have existed for quite a while and continue to increase in attempts and sophistication. It is important to stay aware of the phishing trends and to keep your computer and internet browsers up to date with current antivirus and security patches. These methods may not keep you 100 percent safe, but are the best way to try.
Reference
https://it.sheridancollege.ca/service-catalogue/security/images/phishing-samples/amazon-phish.jpg
Phishing Activity Trends Report. Retrieved from
https://docs.apwg.org/reports/apwg_trends_report_q1_2016.pdf
http://www.phishing.org/history-of-phishing/